LoRa Technology
What is the difference between LoRa® and LoRaWAN®?
LoRa is a wireless technology while LoRaWAN is a network protocol.
To learn more, read the article below.

WHAT IS LORA TECHNOLOGY
LoRa (from "long range") is a physical proprietary radio communication technique.
It is based on spread spectrum modulation techniques derived from chirp spread spectrum (CSS) technology.

WHAT IS LORA WAN
The LoRaWAN network protocol is built on top of the LoRa technique explained above, and it uses the MAC layer as the Media Access Control (MAC) function pair (software layer).
It uses the LoRa modulation. In layman's terms, this means the messages are communicated between network participants or the exchange of messages, using the LoRa modulation.
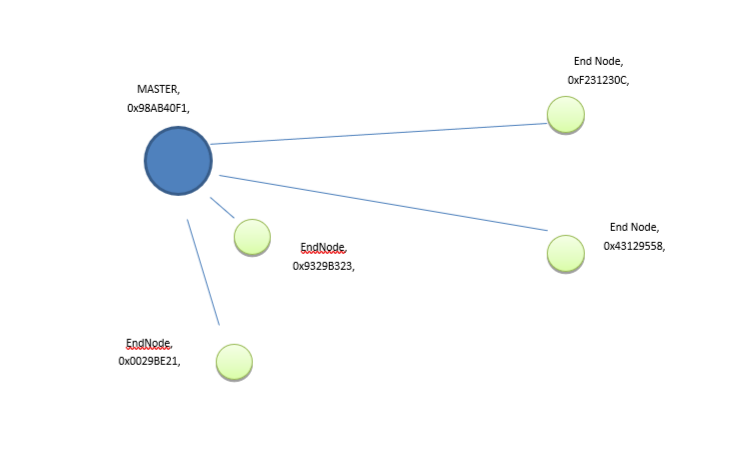
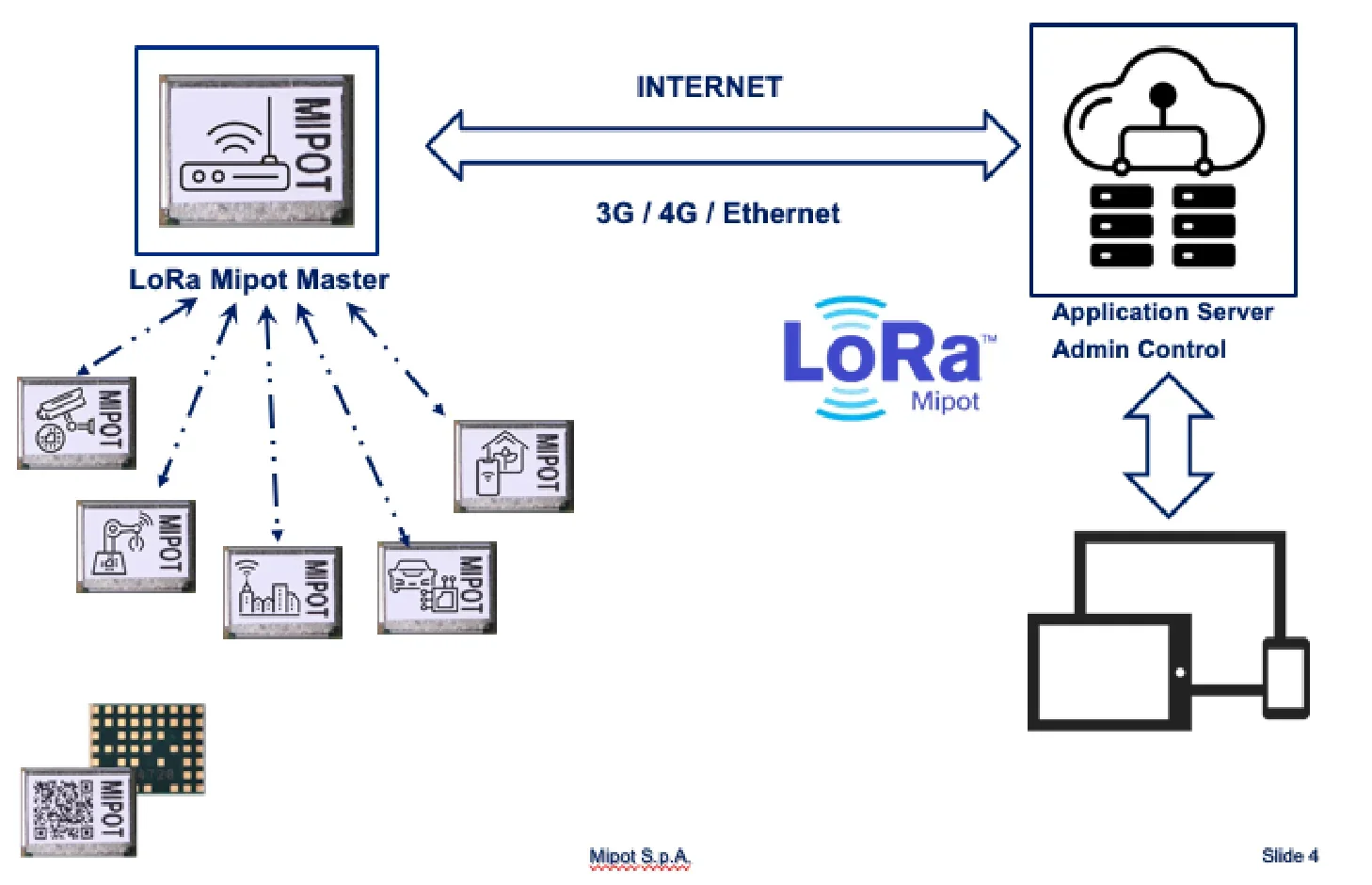
LORA MIPOT: a simple master-slave network with wide coverage
MIPOT LONG RAGE NETWORK is an asynchronous network based on physical layer of LoRa Technology.
Network topology is a star where, in order to minimize power consumption, end nodes work in duty cycle mode.
All messages are cyphered with AES128 encryption algorithm ensuring confidential authentication and integrity during the exchanging of data payload.
The advantages of using the MIPOT LONG RAGE NETWORK are:
- Centralized network: Centralized management helps monitor the network by using the master.
- User-friendly: In star topology, new nodes can be added easily without affecting the rest of the network. Similarly, components can also be removed easily. Hence it is easy to add another computer to the network, and it also becomes easier to replace a malfunctioning unit.
- Very reliable: If one connection or device fails, then all the others will still work. So, the failure of one node or link doesn’t affect the rest of the network.
- Multiple stars can be created to extend the network’s reach: When using star topology, you can extend the length of the network by configuring multiple stars with a central core device in the middle.
LORA MODEM: the possibility for a point-to-point connection with LoRa
A simple stack makes the module with LoRa Technology a RF modem, allowing the user to implement a simple point‑to‑point communication or a more complex custom network (provided that the network protocol is managed on the host device).
All messages can be cyphered with AES128 encryption algorithm ensuring confidential authentication and integrity during the exchanging of data payload.


